Short and complete guide to configure SSH on Cisco router and switch for secure remote connection. The Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. The best-known example application is for remote login to computer systems by users.
SSH provides a secure channel over an unsecured network in a client-server architecture, connecting an SSH client application with an SSH server. Common applications include remote command-line login and remote command execution, but any network service can be secured with SSH. The protocol specification distinguishes between two major versions, referred to as SSH-1 and SSH-2.
The typical use of SSH Protocol
The SSH client sends a packet to the server and hangs for 10 seconds (send packet: type 50) The server response arrives and everything proceeds normally (receive packet: type 51) So, we are waiting for 10 seconds for the server to get back to us with some kind of response (after successfully establishing a TCP connection). Obviously, the packet length must be at least 5 bytes. RFC 4253 specifies that any implementation must support the length of the whole packet to be at least 35000 bytes. Anyway, SSH implementations usually allow for longer packets. OpenSSH/SunSSH accepts length field to be up to 256KB (256. 1024).
The protocol is used in corporate networks for:
- providing secure access for users and automated processes
- interactive and automated file transfers
- issuing remote commands
- managing network infrastructure and other mission-critical system components.
Configure SSH on Cisco Router or Switch
To configure SSH on Cisco router, you need to do:
- Enable SSH on Cisco router.
- Set Password for SSH.
- Force remote access to use SSH.
- Enable Password Encryption.
- Add domain name Server (DNS).
- Add Username and Password.
Let’s enable and configure SSH on Cisco router or switch using the below packet tracer lab. The configure on a packet tracer lab and real Cisco devices are the same. Just try to learn and do it what the SSH remote authentication needs.
Download the packet tracer lab or create your own lab. SSH Configuration Packet Tracer Lab.
In this example, I just enable and configure SSH on SW1 and trying to access it from PC1. It’s enough to learn how to configure SSH on Cisco router.
Ssh Packet Too Long
That’s all. Let’s check the process one by one.
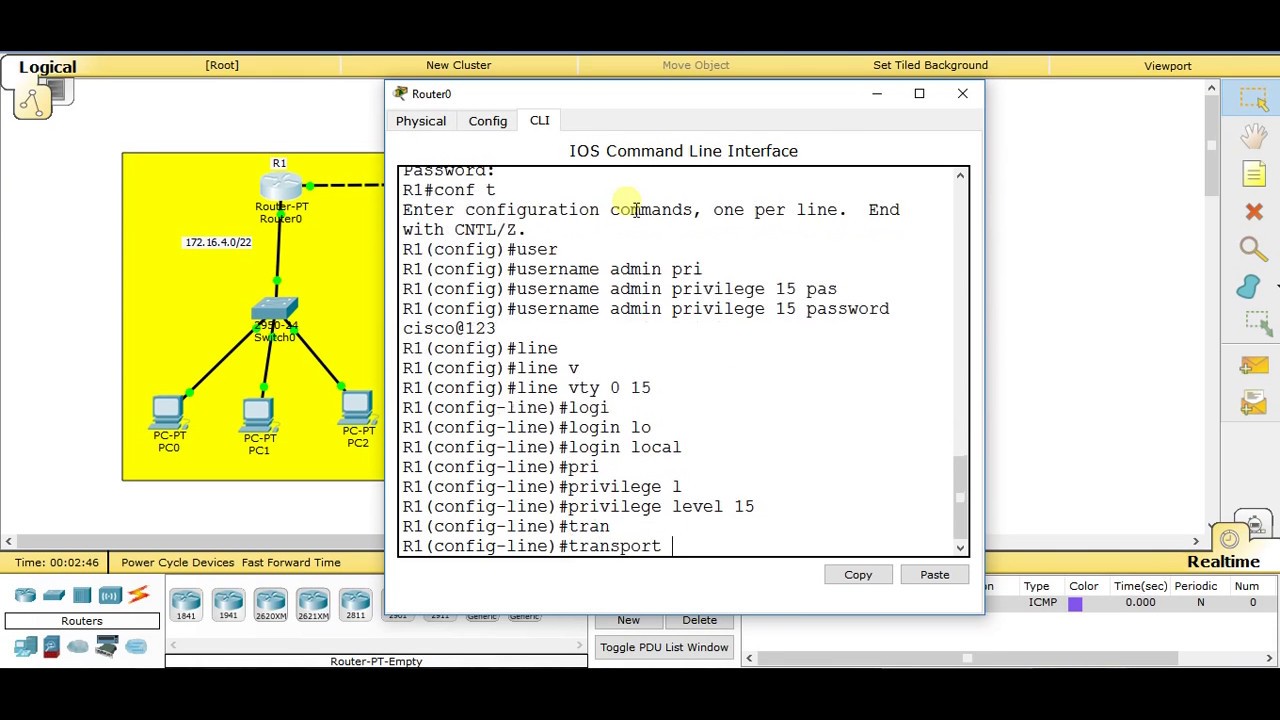
- I have set DNS domain name with “IP domain-name” command.
- Then configure the router to use RSA key pair with modulus size of 1024 bites for remote service authentication with “crypto key generate rsa” command.
- Add username “Admin” with Password of “Technig” for ssh authentication.
- Enabled ssh with “line vty 0 4” command.
- Configure ssh to use local username and password with “login local” command. Remember that you can set a username and password for ssh with “username Admin password Technig” command as well. But here we configure ssh to use local username and password.
- Configure the router to accept only ssh connection with “transport input ssh” command.
- Configure ssh to version 2 using “IP ssh version 2” and set the authentication times to 3 with “IP ssh authentication-retries 3” command.
- Finally set the ssh timeout to 120 seconds with “IP ssh time-out 120” command.
Related Article:Install SSH on CentOS 8.x and Red Hat Linux
The final step is to test the connectivity of ssh from PC1 with “ssh -l Admin 192.168.1.1” command for command prompt.
OK, the ssh works perfectly.

Packet Tracer 1.3.6 Configure Ssh
Sample configuration, setting up SSL to connect to a switch
This configuration applies when you get a new router, and want to create SSH connectivity, so that you don’t need to connect via the console cable.
Step 1. Create a management VLAN and assign it an ip address, so you can connect via IP
vlan 10
exit
int vlan 10
ip address 192.168.1.1 255.255.255.0
no shut
Ssh Packet Size
exit
int fa0/1
switchport mode access
switchport access vlan 10
You should now be able to ping from the PC to the switch.
Ssh Packet Size
Step 2. Configure hostname, domain name, local user, enable password and password encryption
hostname router1
ip domain-name test.com
username steve privilege 15 password happy
enable password veryhappy
service password-encryption
Step 3. Generate crypto keys.
Ssh Packet Tracer
crypto key generate rsa
Ssh Packet Type 51
You are prompted for modulus size. 1024 bits is probably ok.
Step 4. Line vty set up:
# line vty 0 4
(config-line)# transport input ssh
(config-line)# login local
(config-line)# exit
Step 5. Do the same for the console
# line console 0
(config-line)# logging synchronous
(config-line)# login local
Step 6. Connect using the command line on the virtual PC (Command is non standard, in real life you would use PuTTY or similar)

ssh -l steve 192.168.1.1
